What is a Crypto Blockchain 51% Attack? (Compared to 34% Attack?)
Join our Telegram channel for more market analysis & trading tips: t.me/synapsetrading
In theory, any miner can choose to conduct a 51% attack on the network, where they control over 50% of the entire blockchain’s mining power and use it to alter transactions in their favor.
How is this possible?
Blockchain technology has made its mark on the world as one of the major technological advancements of our time, with one of its most famous applications being the decentralized cryptocurrency, Bitcoin.
While blockchain has already revolutionized how people exchange money, we are still just scratching the surface when it comes to what this technology can do.
Blockchain works because it is decentralized — no single entity controls the ledger.
But because of this, blockchain is also more vulnerable to attack than centralized ledgers are.
In this blog post, I will explain everything you need to know about a 51% attack on blockchain, what its impact is, and how it can be prevented.
Let’s jump right into it!
Table of Contents
What is a 51% Attack?
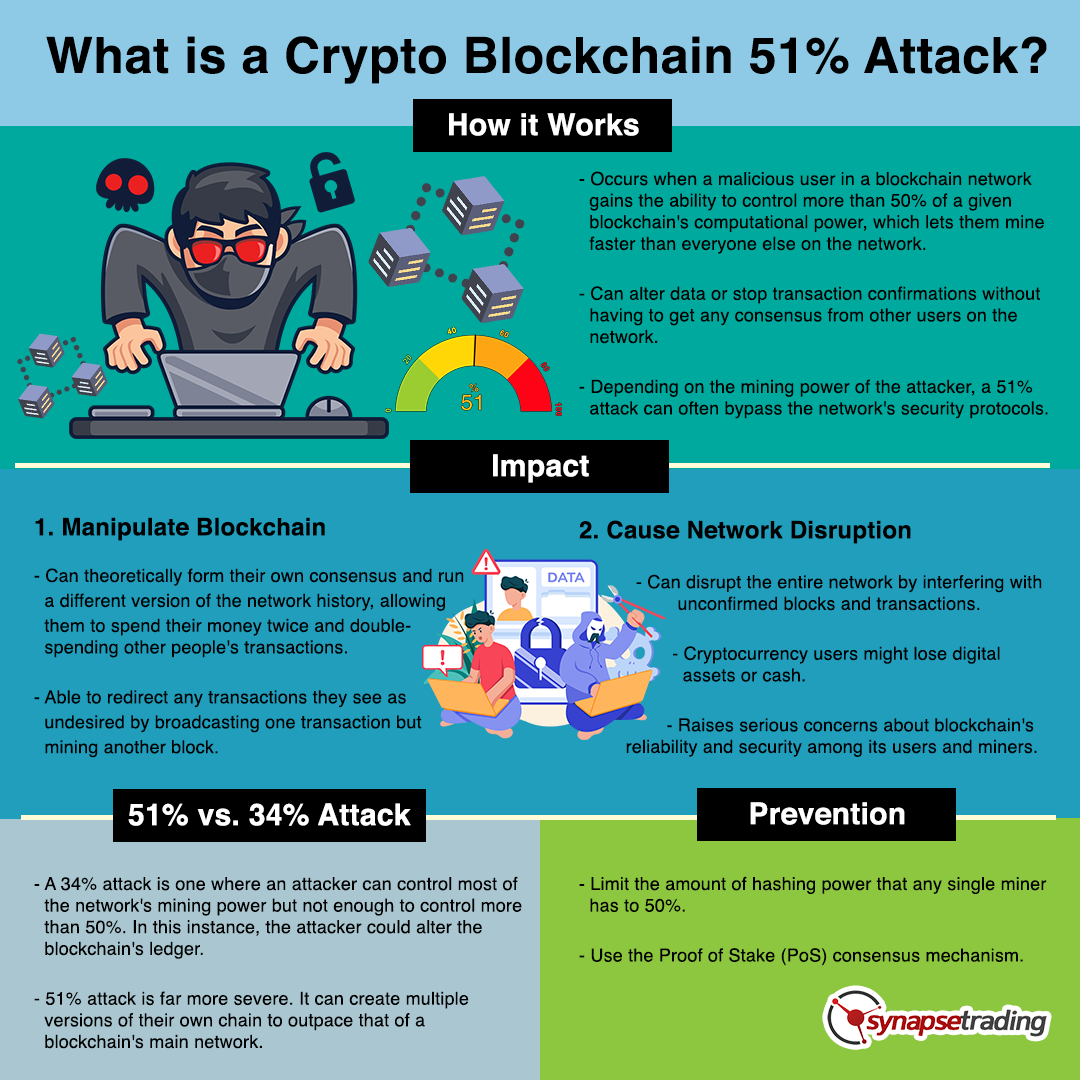
A 51% attack occurs when a malicious user in a blockchain network gains the ability to control more than 50% of a given blockchain’s computational power, which lets them mine faster than everyone else on the network.
This gives them an advantage because they can alter data or stop transaction confirmations without having to get any consensus from other users on the network.
Depending on the mining power of the attacker, a 51% attack can often bypass the network’s security protocols.
While blockchains are generally secure, they are not perfect.
For instance, there is no way to guarantee that all of a blockchain’s participants are honest and will not manipulate transactions or data.
With Bitcoin, miners are in charge of adding new blocks to its blockchain and validating transactions.
Because they decide which transactions to validate, they can choose not to include some that their users want validated if it helps them get ahead.
But this isn’t a problem with most cryptocurrencies, including Bitcoin and Ethereum, because the computing power needed to attack such a huge established blockchain would be impossibly large.
We only see this type of behavior during so-called penny wars.
These occur when small players try to game the system by spamming large numbers of unimportant transactions to push up the price paid per kilobyte (KB) for mining these low-value transactions.
To combat such attacks, most blockchains also have built-in features and hard fork protocols that enforce changes in their system if necessary.
What is the Impact of a 51% Attack?
If miners get too much hash rate and collectively control more than 50%, they can theoretically form their own consensus and run a different version of the network history, allowing them to spend their money twice and double-spending other people’s transactions.
They would also be able to redirect any transactions they see as undesired by broadcasting one transaction but mining another block.
All these changes could impact end users because they allow an entity with majority mining power to manipulate the blockchain and its rules in ways incompatible with end-user expectations.
This kind of attack is why some people advocate for Segregated Witness (SegWit) or Lightning Network to handle Bitcoin transactions instead of on-chain transactions, as there would not be any need for a lot of hashing power to execute these types of transactions.
A 51% Attack Can Cause Network Disruption
One of the primary Blockchain protocols is referred to as Proof-of-work (PoW), which is used by Bitcoin, Ethereum, and other popular networks.
The PoW protocol essentially maintains that every 10 minutes, there will be new blocks added to a blockchain’s ledger.
For someone in a network to add new blocks to that blockchain, they must guess complex mathematical equations, which are nearly impossible to calculate if you don’t have access to high computing power.
However, in a 51% attack, the attacker can disrupt the entire network by interfering with unconfirmed blocks and transactions.
Cryptocurrency users might lose digital assets or cash due to a 51% attack.
This raises serious concerns about blockchain’s reliability and security among its users and miners.
Is the Damage Permanent?
It is important to note that while these types of malicious actors might be able to disrupt a blockchain and invalidate recent transactions temporarily, they do not necessarily have access to modify past transactions.
So even though it may seem like your money has disappeared forever during one of these attacks, rest assured that it won’t stay gone forever.
For example, if someone transferred Bitcoin to another individual or merchant, it would not be possible for an attacker to reverse that transaction.
They could still prevent future transactions from going through and might even be able to access your funds, but these are two different things entirely.
Once these attacks have ended, you will regain access to your funds.
How Different Is It from a 34% Attack?
A 34% attack is one where an attacker can control most of the network’s mining power, but does not have enough to control more than 50%.
In this instance, the attacker could alter the blockchain’s ledger.
The consequences of a 51% attack are far more severe.
A 51% attack would not stop transactions from happening, but it could severely disrupt blockchain’s peer-to-peer model and open doors for double-spending.
With more than half of all computing power available to an attacker, they could create multiple versions of their own chain to outpace that of a blockchain’s main network.
51% Attacks in Recent Times
a) Grin:
Grin, a blockchain cryptocurrency focused on preserving the privacy of its users, was the currency on the attack where an unknown miner took up 57% of the Grin hash power.
What the attacker intended is still a mystery.
Grin was forced to shut off payouts and urged miners to stop until the issue was fixed.
Grin later re-established the network and added additional measures to prevent the attack from recurring.
b) Vertcoin:
The cryptocurrency Vertcoin has been attacked several times over the past few years.
In one such attack, the attackers wrote their own blocks in place of the Vertcoin genuine blocks.
Vertcoin switched from the original blockchain to a new, more robust PoW system to keep attackers from double spending and getting their hands on users’ hard-earned money.
Moreover, it had to cut off powerful mining chips to keep its mining more community-based.
c) Bitcoin Gold:
Compared to other Bitcoin forks such as SHA-256, Bitcoin Gold (BTG) implements the Equihash consensus algorithm.
The developers intended to achieve decentralization by using GPU mining instead of ASICs.
However, an unknown miner managed to gain access to more than 51% of the overall BTG hash rate in 2018, resulting in heavy losses for the network.
Another 51% attack on BTG occurred in 2020, and the network experienced two reorganizations in two days.
An enormous amount of money was double spent.
There was a suspicion that the BTG network had ASIC mining devices that might have been hidden from the community.
The community then urged the blockchain to implement a more secure algorithm.
d) Ethereum Classic:
In 2020, the ETC blockchain was attacked three times in the same month.
ETC relies on the decentralized proof-of-work (PoW) consensus algorithm, just like Bitcoin, which makes it challenging to avoid or mitigate 51% attacks.
Though these attacks did not significantly affect ETC prices, they reduced users’ trust in the network.
Can a 51% Attack Be Prevented?
Although blockchain is a decentralized database, it is not immune to hacking.
The best way to protect against a 51% attack is to limit the amount of hashing power that any single miner has to 50%.
So no person or organization can control more than 50% of the total network’s mining power.
Another way to prevent a 51% attack is using the Proof of Stake (PoS) consensus mechanism.
PoS makes it more difficult for validators (not miners) to produce blocks and act maliciously because they don’t have an incentive to do so.
Instead, the validator’s stakes are at stake — their investment in the cryptocurrency.
For them to abuse their power, they would have to forfeit their entire stake.
The higher the stakes, the more difficult it becomes for them to act maliciously.
Concluding Thoughts
When blockchain was first introduced, it caused quite a buzz in the financial sector.
Because of its decentralized, trustless nature, this technology has captured everyone’s attention and promises to have a far-reaching impact on many aspects of everyday life.
However, blockchain isn’t infallible, and like any other technology, it has its vulnerabilities and risks that users should be aware of, such as the 51% attack and 34% attack.
Now that I have covered all you need to know about a crypto blockchain 51% attack, are you able to tell which new tokens are at risk of such attacks?
Do you think the upcoming new security protocols will be able to stop such attacks in future?
Let me know in the comments below.

If you would like to learn more about crypto & DeFi, also check out: “The Ultimate Guide to Blockchain & Cryptocurrencies”
 Our flagship mentoring program is suitable for both beginners and advanced traders, covering the 4 strategies which I used over the past 15 years to build up my 7-figure personal trading portfolio.
Our flagship mentoring program is suitable for both beginners and advanced traders, covering the 4 strategies which I used over the past 15 years to build up my 7-figure personal trading portfolio.
 If you're looking for a reputable brokerage that covers all products (SG stocks, US stocks, global stocks, bonds, ETFs, REITs, forex, futures, crypto) and has one of the lowest commissions, this is what I currently use.
If you're looking for a reputable brokerage that covers all products (SG stocks, US stocks, global stocks, bonds, ETFs, REITs, forex, futures, crypto) and has one of the lowest commissions, this is what I currently use.
After trading for 18 years, reading 1500+ books, and mentoring 1000+ traders, I specialise in helping people improve their trading results, by using tested trading strategies, and making better decisions via decision science.













Leave a Reply
Want to join the discussion?Feel free to contribute!